Corrado Giustozzi, renowned cybersecurity expert, will be interviewed on Radio 24 in the broadcast of Enrico Pagliarini to discuss the recent issues related to crowdstrike and Windows systems. During the interview, Giustozzi will deepen the details of the bug that hit the protection software crowdstrike Falcon

095 RADIO 24 – WITH ENRICO PAGLIARINI | CrowdStrike Outage: A “Buggy” Update Disrupts Windows PCs Worldwide
- What caused the problem that is paralyzing the world?
- Friday, July, 19
- Speakers/Guests: Corrado Giustozzi
- Radio 24

095 AWS Public Sector Security Day | Roma
- Securing the Future of Urban and Energy Technologies
- Thursday, July 11, 2024
- 9:30 AM - 5:00 PM
- Speakers/Guests: Corrado Giustozzi
On July 11, 2024, Rome will host the AWS Public Sector Security Day, a premier event focused on the latest advancements in cloud security practices. This event, held at the Grand Hotel Palace, will gather experts and professionals in the field of cybersecurity to discuss challenges and opportunities in digital security, with a particular emphasis on new technologies and innovative solutions.
Corrado Giustozzi, a renowned cybersecurity expert, will be a key discussant at the event, offering his extensive experience and knowledge on the subject. His participation will provide valuable insights into the evolving landscape of cybersecurity and the best practices for securing public sector applications.
- Grand Hotel Palace Rome, Via Vittorio Veneto, 70, 00187 Roma RM, Italy

094 Technical Table: Innovation and Security between Smart City and Smart Energy
- Securing the Future of Urban and Energy Technologies
- Wednesday, July 10, 2024
- 10:30 AM - 1:00 PM
- Speakers/Guests: Corrado Giustozzi
The National Association of Young Innovators, in collaboration with Alé Comunicare per Strategie, announces a technical roundtable on “Innovation and Security in Smart Cities and Smart Energy.” This event will delve into topics related to smart cities and smart energy, focusing on security and technological innovation.
Key speakers, including Corrado Giustozzi, a renowned cybersecurity expert, will share their insights. The roundtable aims to foster constructive debate and idea exchange among participants, addressing current and future challenges in implementing advanced technologies.
- Camera dei Deputati, Piazza del Parlamento 24, Rome

093 Cyber Attacks on Companies: Understanding to Defend
- A Phenomenon to Understand to Defend Against
- Tuesday, July 2, 2024
- 4:30 PM - 6:30 PM
- Speakers/Guests: Mauro Cicognini
This event focuses on the critical topic of cyber attacks on companies, featuring contributions from the Postal and Communications Police, industry experts, and academia. Key sessions include state-of-the-art updates, corporate testimonials, academic research, and the objectives of Clusit. Mauro Cicognini, a member of the Clusit technical committee, will also speak on the activities and goals of Clusit.
- Sala Eventi Tecnopolo di Modena, Via P. Vivarelli 2, Modena

092 Privacy on the Road on the Beach – Fourth Edition
- Combatting Cyber-Mafia: The New Frontier of Organized Crime
- Friday, June 28, 2024
- 3:00 PM
- Speakers/Guests: Corrado Giustozzi
The fourth edition of “Privacy on the Road on the Beach” will feature Corrado Giustozzi, Founding Partner & Chief Strategist at Rexilience, discussing the battle against cyber-mafia and the evolving landscape of organized crime in the digital age. This event is part of a series dedicated to enhancing privacy and cybersecurity awareness.
- Bagni 49/50, Lungomare Augusto Murri 24, Rimini (RN)

091 AI and Cybercrime Webinar: Real Threats and Defense Enhancement
- Exploring AI in Law Enforcement and Cybersecurity
- Monday, June 24, 2024
- 9:30 AM - 12:30 PM
- Speakers/Guests: Corrado Giustozzi
The ongoing webinar series continues with a session on “AI and Cybercrime – Real Threats and Defense Enhancement,” part of the National Cybersecurity Strategy 2022-2026. This event, organized by the Ministry of Enterprises and Made in Italy and the Scuola Superiore di Specializzazione in Telecomunicazioni, will feature key speakers including Corrado Giustozzi, Founding Partner & Chief Strategist at Rexilience, discussing “Limits and Vulnerabilities of AI.”
- Online Webinar

090 RADIO 24 – WITH ENRICO PAGLIARINI | Discussing Cybersecurity
- Analysis of the Italian cybersecurity landscape
- Friday, June 21, 2024
- Speakers/Guests: Corrado Giustozzi
On June 21, 2024, Corrado Giustozzi, Chief Strategist at Rexilience, was a guest on Enrico Pagliarini’s show “2024” on Radio24. During the program, Giustozzi provided an in-depth analysis of recent cybersecurity incidents, highlighting key trends and potential vulnerabilities.
- Radio 24

089 Security Summit Roma 2024: Insights and Trends in Cybersecurity
- Understanding the Challenges of AI in Public Administration
- Wednesday, June 19, 2024
- 9:00 AM - 5:00 PM
- Speakers/Guests: Corrado Giustozzi
The Security Summit Roma 2024, organized by Clusit, focuses on the latest trends and challenges in cybersecurity. This event brings together top experts to discuss cyber threats, resilience, and defense strategies, specifically for public administration, defense, and healthcare sectors.
Corrado Giustozzi, a renowned cybersecurity expert and Clusit Executive Committee member, will moderate the plenary session. This session will present the latest data from the Clusit Report 2024, offering an in-depth analysis of recent cybersecurity incidents and trends, essential for industry professionals and policymakers.
- Auditorium della Tecnica, Confindustria, Rome

088 Privacy Symposium 2024
- The future of Cybersecurity and AI Compliance
- June 10-14, 2024
- Speakers/Guests: Mauro Cicognini
The Privacy Symposium 2024 is a premier event focusing on the latest developments in data protection, cybersecurity, and AI compliance. The symposium will feature over 140 sessions with more than 300 expert speakers from around the globe, aiming to foster international dialogue, cooperation, and knowledge-sharing on data regulation and innovative technologies.
Mauro Cicognini, Founder Partner at Rexilience, will moderate some sessions, which will delve into critical aspects of cybersecurity and AI regulation, offering insights from leading industry experts and practitioners.
- Palazzo dei Congressi, Rome, Sala Academy 2

087 VIII Open Day: Alienation and Acceleration – Dignity of Man between Prison and Artificial Intelligence
- Exploring the Intersection of Human Dignity, Incarceration, and Artificial Intelligence
- Friday, June 07 2024
- 05:00 PM
- Speakers/Guests: Corrado Giustozzi
The VIII Open Day organized by the Union of Italian Criminal Chambers (UCPI) will focus on the theme “Alienation and Acceleration: Dignity of Man, between Prison and Artificial Intelligence.” The event will address issues related to incarceration, the principle of humanity in sentencing, and the opportunities, uses, and distortions of artificial intelligence and its impact on the right to a fair trial. Corrado Giustozzi, Chief Strategist at Rexilience, will be among the speakers, contributing his expertise on the vulnerabilities of AI in this context.
- Palacongressi, Via della Fiera, 23, Rimini

086 Forum PA 2024: Limits and Vulnerabilities of AI
- Understanding the Challenges of AI in Public Administration
- Wednesday, May 22, 2024
- 05:30 PM - 06:20 PM
- Speakers/Guests: Corrado Giustozzi
The Forum PA 2024 will feature Corrado Giustozzi, Chief Strategist at Rexilience and a member of the Executive Board of Clusit, who will address the “Limits and Vulnerabilities of AI”. This session will explore the inherent limitations and potential risks associated with artificial intelligence, especially in the context of public administration.
- Palazzo dei Congressi, Rome, Sala Academy 2

085 Exploring MDR Services: Opportunities or Risks for MSSP Partners?
- Scenarios, Trends, and Prospects in Italian Security
- Tuesday, May 21, 2024
- 9:30 AM - 01:00 PM
- Speakers/Guests: Corrado Giustozzi
The event “Exploring MDR Services: Opportunities or Risks for MSSP Partners?” will feature Corrado Giustozzi, Founding Partner & Chief Strategist at Rexilience, as the host and moderator. Giustozzi will engage attendees with insights on the latest scenarios, trends, and prospects in the Italian security landscape. This event, organized by ESET Italia, aims to explore the benefits and potential risks of Managed Detection and Response (MDR) services for Managed Security Service Providers (MSSP).
- Excelsior Hotel Gallia, Piazza Duca d'Aosta, 9, Milan

084 Legal Breakfast Bytes: Data Protection and Compliance
- Cybersecurity and integrated compliance: impacts on business organization and operating procedures
- Monday, May 6, 2024
- 8:30 AM
- Speakers/Guests: Corrado Giustozzi
The Legal Breakfast on Data Protection and Compliance hosted by Ristuccia Tufarelli will cover the latest developments in data protection laws and regulatory compliance, providing valuable insights for professionals dealing with legal and regulatory frameworks. Corrado Giustozzi, from Rexilience, will be a key speaker, discussing critical aspects of cybersecurity and data protection.
- Piazza Cavour, 17 - Rome

083 Exhibition at Rexilience: the Artistic Treasures of Comics
- Original Works by Crepax, Pratt, Magnus, Pazienza, and Quino
- Sunday, May 5, 2024
- 03:00 PM
- Speakers/Guests: Angelomario Moratti
Join us at Rexilience in Milan for a special exhibition organized in collaboration with Krazy Art Gallery. Curated by Michele Ulysse Lipparini and Giulia Parodi, this event offers a unique opportunity to explore the precious original works of renowned artists such as Crepax, Pratt, Magnus, Pazienza, and Quino. This exhibition is part of the Open Museums initiative, providing a rare glimpse into the creativity and mastery of these legendary artists.
- Rexilience - Corso Venezia, 54 (P. 3), Milan

082 Innovation Cybersecurity Summit – 4th Edition
- Prospective and Applications for New Assets in Cybersecurity, Energy Defense, and Aerospace
- Tuesday, April, 16 2024
- 09:00 AM
- Speakers/Guests: Corrado Giustozzi
Join Corrado Giustozzi, Senior Cyber Security Strategist, at the 4th Edition of the Innovation Cybersecurity Summit. This event will explore the latest prospects and applications in cybersecurity, energy defense, and aerospace, set against the prestigious backdrop of the Circolo Ufficiali Forze Armate d’Italia in Rome. The summit is an essential gathering for professionals seeking to stay abreast of the latest advancements in cybersecurity. Attendees will gain valuable insights into new strategies and technologies that can be applied to protect critical assets in the energy and aerospace sectors.
- CUFA – Circolo Ufficiali Forze Armate d’Italia, Via Venti Settembre, 2, Rome

081 Unem Seminar on New Cybersecurity Obligations in the Fuel Sector
- Addressing Cybersecurity Challenges in Critical Infrastructures
- Monday, April, 15 2024
- 02:30 PM - 05:00 PM
- Speakers/Guests: Corrado Giustozzi
Today in Rome, a prestigious seminar on cybersecurity will take place, opened by Gianni Murano, President of UNEM. The event will feature notable speakers including Corrado Giustozzi from Rexilience and Simonetta Sabatino from Saras. They will discuss the latest cybersecurity obligations and challenges faced by the fuel sector.
- UNEM, Piazzale L. Sturzo 31, Rome (Hybrid Mode: In-person and Zoom)

080 Cybersecurity: Legal and Applicative Profiles
- Citizens, Businesses, and Administrations
- Friday, April, 12
- 03:00 PM - 06:00 PM
- Speakers/Guests: Corrado Giustozzi
Corrado Giustozzi, Founding Partner and Chief Strategist at Rexilience, will be a key speaker at this event organized in collaboration with the University of Bari. He will discuss “Cyber Attacks in Supranational Balances,” addressing the complex dynamics of cyber threats on an international scale.
- Department of Political Science, Aula Starace, University of Bari

079 RADIO 24 – WITH ENRICO PAGLIARINI | The Almost Catastrophe of Linux
- The Discovery of a Critical Vulnerability in Linux
- Friday, April, 05
- Speakers/Guests: Corrado Giustozzi
The largest attempted sabotage in Linux history was thwarted thanks to the timely discovery of a backdoor by engineer Andres Freund. If exploited, the vulnerability could have had devastating global consequences. Corrado Giustozzi will delve into the technical details of the attack, its implications, and the security measures needed to prevent future incidents.
- Radio 24

078 AI Forum Milan: Innovations and Challenges in Artificial Intelligence
- Artificial Intelligence and Technological Innovation: Synergies and Challenges
- Thursday, April, 4
- 16:00
- Speakers/Guests: Stefano Quintarelli
During the AI Forum in Milan, Stefano Quintarelli, will participate in a panel discussion on “AI or Technology.” This meeting will engage experts and industry leaders who will discuss the impact of artificial intelligence on organizations and business, exploring how this technology can be integrated into business strategies to maximize efficiency and innovation.
- Security Summit Milano
- Palazzo Mezzanotte, Milan

077 RADIO 24 – WITH ENRICO PAGLIARINI | Omomorphic cryptography
- cybersecurity technological innovations
- Friday, March 15
- Speakers/Guests: Corrado Giustozzi
On Friday, March 15, Corrado Giustozzi will be Enrico Pagliarini’s guest on Radio24 to discuss homomorphic cryptography and its applications in cybersecurity. The episode will also cover the passage of the AI Act and the week’s top innovation and technology news
- Radio 24

076 One hundred years of innovation
- The contribution of the University of Milan to the socioeconomic fabric of Italy
- Friday, March 22
- 11:40
- Speakers/Guests: Marco Locatelli e Stefano Quintarelli
Celebrating 100 years of innovation at the University of Milan, Stefano Quintarelli and Marco Locatelli together with Alberto Fioravanti, moderated by Prof. Gian Paolo Rossi, spoke about their experience:
“Città Studi Valley: university-born digital entrepreneurship.”
- Università degli Studi di Milano (Sala Napoleonica)
- Milan, Via Brera 28

075 A synergistic approach between cybersecurity and personal data protection
- Thursday, March 21
- 14:00
- Speakers/Guests: Alessandro Vallega and Stefano Moni
Personal data protection is not an exclusively legal discipline. An open approach to the different facets of this complex world is necessary to understand and address the challenges posed by having to safeguard fundamental rights.
- Security Summit Milano
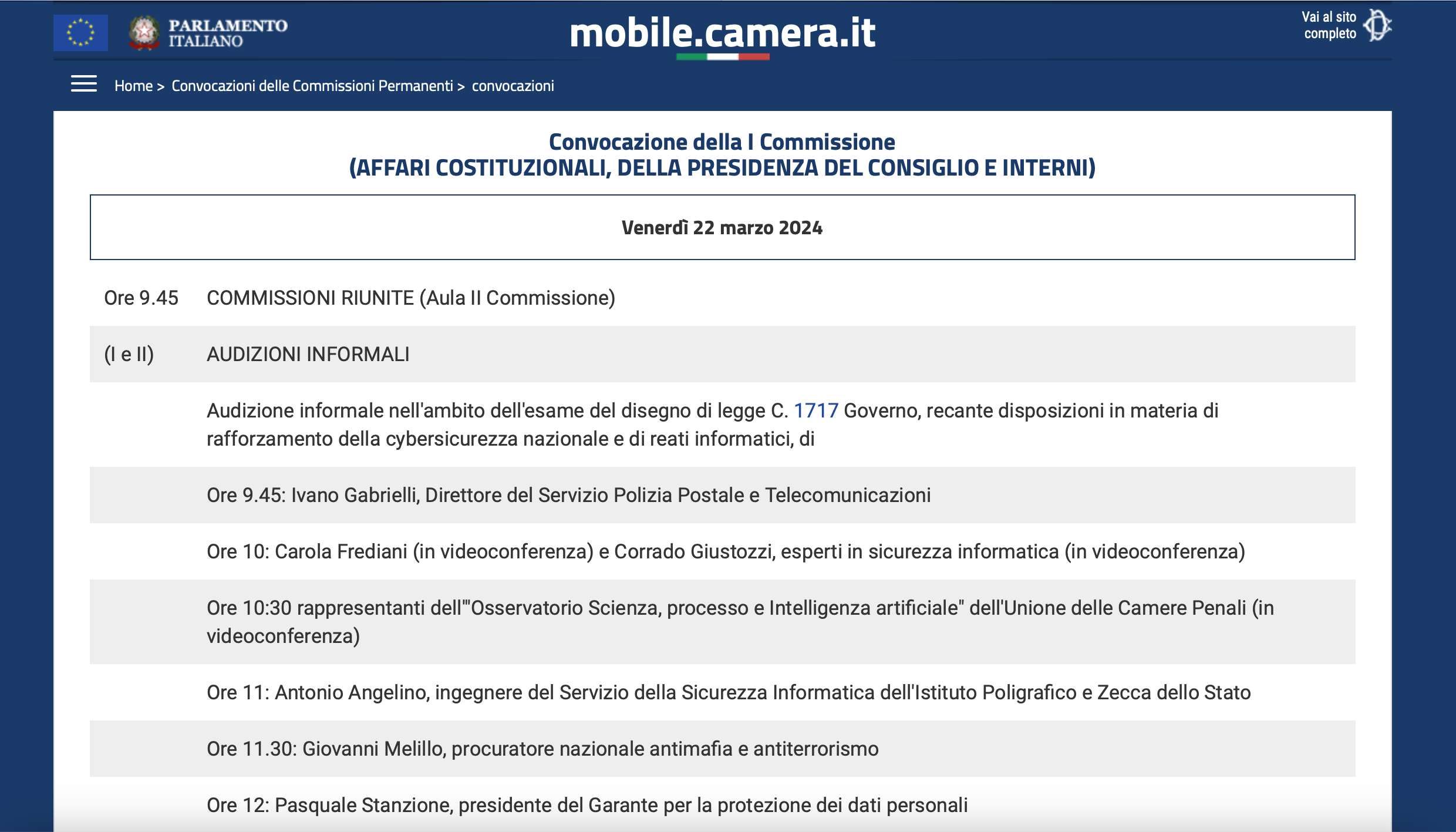
074 Strengthening National Cybersecurity
- Convocation of the I Commission (AFFARI COSTITUZIONALI, DELLA PRESIDENZA DEL CONSIGLIO E INTERNI)
- Friday, March 22
- 10:00
- Speakers/Guests: Corrado Giustozzi
Corrado Giustozzi was heard by the Joint Committees I Constitutional Affairs and II Justice of the Chamber of Deputies as part of the examination of Bill C. 1717 Government, on provisions for strengthening national cybersecurity and cybercrimes.
- Online
073 Integrated cybersecurity and compliance
- Impacts on business organization and operating procedures
- Thursday, March 21
- 8:30-11:00
- Speakers/Guests: Corrado Giustozzi
Corrado Giustozzi CHIEF Strategist REXILIENCE journalist and writer, lecturer in Cybersecurity in the MSc in Intelligent Systems Engineering at Campus Bio-Medico, and in the Level I and II Masters in Cybersecurity at LUISS, Campus Bio-Medico, Link and SIOI participated in the morning meeting “Legal Breakfast Bytes” with professionals Luca Tufarelli, Francesca Rosetti and Maria Lilia La Porta of Studio Tufarelli Ristuccia and Partners, to explore topical issues with a breakfast together. During this meeting, some topics introduced in the previous meeting were discussed and taken up again, concerning: computer crimes, Cybersecurity and Model 231.
- Piazza Cavour, 17 Roma

072 CambierAI
- The New Challenges of Generative Artificial Intelligence.
- Wednesday, March 20, 2024
- 16:30
- Speakers/Guests: Stefano Quintarelli
Generative artificial intelligence is constantly evolving, with significant implications for several disciplines. In this session, which closes the second day of the Security summit, largely dedicated to AI, we explore from different perspectives (technological, social, philosophical and economic…) the emerging challenges in this area, analyzing new frontiers and innovative perspectives. Central are issues such as ethics in the use of generative models, interpretation and understanding of the results produced, responsible creation of digital content, and security and privacy in the implementation of advanced generative algorithms.
- Security Summit Milano

071 Step-by-step cyber attack
- A journey through security technologies and services
- Wednesday, March 20, 2024
- 9:20
- Speakers/Guests: Mauro Cicognini
Analysis of the Technical Tactics and Procedures (TTP) of an attack, by the Managed Detection and Response (MDR) team through ESET XDR and Endpoint technologies. Through a step-by-step analyzed attack, it will be shown how an MDR service, with supporting XDR telemetry and Endpoint Protection, allows attackers’ tactics to be analyzed in order to detect, block, and remediate a security incident.
- Security Summit Milano

070 AI: How not to have your job stolen by the algorithm
- A coffee with the club
- Tuesday, March 19, 2024
- 17:00
- Speakers/Guests: Corrado Giustozzi
Artificial intelligence is transforming the world at a dizzying pace: AI is revolutionizing the world in which we live, work and interact with the world around us.
- Circolo Giuristi Telematici Roma

069 Intelligence repot
- New attack vectors and business models of cybercrime
- Tuesday, March 19, 2024
- 12:00
- Speakers/Guests: Mauro Cicognini
Illegally stolen information is sold with different schemes to the past; business models evolve favoring subscription subscriptions. Exactly the same as in the legal economy! RaaS, MaaS, toolkits, and associated services are frantically evolving.
- Security Summit Milano

068 AI: instructions for use
- Friday, March 8, 2024
- Speakers/Guests: Corrado Giustozzi
On Friday, March 8, the first meeting of the cycle Tech talk – Meetings with the protagonists of the debate on technology and digital organized as part of the training activities of the Parliamentary IT Cluster was held at the Camera dei deputati. Our own Corrado Giustozzi gave his thoughts on the topic of “AI: instructions for use.”
- Camera dei deputati

067 Convention Nazionale CSQA Certificazioni
- Monday, January 8, 2024
- Speakers/Guests: Corrado Giustozzi
On Monday, Jan. 8, Corrado Giustozzi, chief strategist of Rexilience, will participate as a speaker at the CSQA Certifications National Convention with a talk on the topical issue : “Vulnerabilities and Risks in AI Systems.”
- Online

066 Radio24: Westpole ransomware attack
- Case of the month
- Friday, December 22, 2023
- Speakers/Guests: Corrado Giustozzi
On Friday, December 22, Corrado Giustozzi, host of Enrico Pagliarini, accurately and thoroughly analyzed on Radio24 the ransomware attack suffered by Westpole for the serious consequences on Italy.
- Radio24

065 OPEN IA: PODCAST
THE RISK OF MONOPOLISMS IN IA
- Radio Svizzera Italiana
- Friday, November 24, 2023
- 12:30
- Speakers/Guests: Corrado Giustozzi
On Friday, November 24, Corrado Giustozzi joined the Alphaville broadcast on Italian Swiss Radio to discuss the dark affairs of OpenAI live.
- Web Radio Streaming

064 IEA Convention Fall 2023
- Istituto Superiore di Sanità di Roma
- Tuesday, November 14, 2023
- 12:00
- Speakers/Guests: Corrado Giustozzi
Corrado Giustozzi will speak at the second day of the Fall Conference of the Italian Association of Epidemiology at the Istituto Superiore di Sanità in Rome.
His presentation, “Limits and Vulnerabilities of Artificial Intelligence,” will open the section dedicated to “Reflections on Data Security, Ethics and Digital Health: an Integrated Framework.”
- Rome, Istituto Superiore di Sanità
- Viale Regina Elena 299

063 Webinar “Introduction to the Cloud. Risks to Consider”
- Cloud risks and opportunities
- Friday, November 10, 2023
- 14:30
- Speakers/Guests: Alessandro Vallega
The Cloud has been increasingly adopted by companies for many years, but many have yet to understand its best use and the risks that can result from misuse. In the webinar held by Alessandro Vallega, the meaning of Cloud (in its different forms) was defined, how it can be used and what steps are best to take to avoid any dangers in terms of security and compliance.
- Osservatori.net

062 CLUSIT Security Summit Streaming Edition 2023
- How is the scenario evolving? Global and national cybersecurity in the first 6 months 2023
- Thursday, November 9, 2023
- 9:00
- Speakers/Guests: Corrado Giustozzi
On Thursday, November 9, Corrado Giustozzi, along with other authors of the “Clusit Report 2023 on ICT Security in Italy,” presented the new CLUSIT report with data analysis of attacks that occurred in the first half of 2023.
- Online

061 Forensic Training
- Laboratori Cagliaritani
- Friday, November 3, 2023
- 17:30
- Speakers/Guests: Corrado Giustozzi
The legal profession in the age of artificial intelligence.
- Cagliari
- T-HOTEL

060 ISPI: Security risk
- European security impacts of terrorist risk
- Monday, October 30 2023
- 18:00
- Speakers/Guests: Corrado Giustozzi
On Monday, October 30, Corrado Giustozzi participated, along with authoritative experts, in the episode of ISPI-Institute for International Policy Studies’ The World This Weekdedicated to delving into the impacts on European security of the terrorist risk resulting from the escalating conflict between Israel and Hamas.
- online - YouTube

059 Festival of Diplomacy
- The geopolitical challenge of quantum supercomputers
- Wednesday 27 October 2023
- 14:00
- Speakers/Guests: Corrado Giustozzi
As part of the Festival of Diplomacy 2023, Corrado Giustozzi at the Center for American Studies in Rome participated in a discussion on “The Geopolitical Challenge of Quantum Supercomputers.”
The event was held in English, and it was possible to participate in person or via live streaming.
- Roma
- Via Michelangelo Caetani 32

058 Cybersecurity:
- Practical guide for your organization
- 19/10/2023
- 14:30-18:30
- Speakers/Guests: Mauro Cicognini
Along with the many opportunities, the digital transition also brings risks, including potential threats from cyber attacks. Increasingly, therefore, we are hearing more and more about Cyber Security, perhaps not fully understanding that taking cover from cybercrime protects against operational and production downtime, safeguards corporate reputation, and guards against possible financial loss, all to ensure business continuity.
Mauro Cicognini,Senior Partner of Rexilience and Member of the Scientific Committee of Clusit speaks about”: Are Italian companies prepared for cyber incidents? Some answers from the Clusit Report data.”
- ComoNExT - Innovation Hub
- Via Cavour 2, 22074 Lomazzo

057B ROMA CITTA’ CAPITALE
- Digital Cities
- October 18, 2023
- 8:00
- Speakers/Guests: Corrado Giustozzi
Centre of gravity between regulations, technologies, cybersecurity and personal rights
Will attend:
- Roberto Gualtieri. Mayor of Roma Capitale
- Lamberto Giannini, Prefetto di Roma
- Bruno Frattasi, Director General of the National Cybersecurity Agency
- Monica Lucarelli, Councillor for Security Policies
- … and many other leading participants (see attached brochure)
- Roma
- Sala Protomoteca - Campidoglio

057 INSECURITY AND RELIABILITY OF ARTIFICIAL INTELLIGENCE
- Virtual Round table ASSI
- 12/10/2023
- 18:00
- Speakers/Guests: Corrado Giustozzi
Artificial Intelligence (AI) , with its applications, enters business processes, simulations, video surveillance, entertainment, medicine, mobility, smart cyties etc … even the war industry.
Corrado Giustozzi,Founding Partner & Chief Strategist, Rexilience, speaks at the ASSI “virtual” Roundtable.
- ASSI Youtube channel
- https://assi-bo.it/insicurezza-e-affidabilita-dellintelligenza-artificiale/

056d AI: Hype and Reality
- Navigating the Artificial Intelligence landscape
- October 10, 2023
- 14.50
- Speakers/Guests: Mauro Cicognini
Artificial intelligence technologies are a powerful tool in the hands of cyber criminals who use this technology to refine, speed up and extend cyber attacks on a large scale. While there is enthusiasm among the ‘BlackHats’ for the advent of WormGPT, the ‘good guys’ must quickly discuss the pressing need to transform traditional security systems to integrate AI-equipped defensive strategies. What does the future hold for us and how do IT companies need to adapt to this paradigm shift? We will see what proactive measures can be taken to reduce the initial attack surface for cybercriminals, especially for companies that do not have sufficient resources or do not yet use an artificial intelligence engine to defend themselves. In addition, we will explore how to improve the efficiency of incident response and enhance cybersecurity readiness.
- Verona
- Via Belgio 16, 37135

056c The abuse of vulnerable drivers (BYOVD)
- An increasingly popular and handy technique
- October 10, 2023
- 14.00
- Speakers/Guests: Mauro Cicognini
The abuse of vulnerable drivers, known as BYOVD (Bring Your Own Vulnerable Driver), has emerged in recent years as an increasingly common and accessible attack technique. This methodology exploits any vulnerabilities in the drivers to gain full access to the systems’ memory and evade defence mechanisms. With the wide availability of vulnerable third-party drivers and tools that can exploit them, such attacks are becoming a significant threat to the security of data and IT infrastructures. The methods used by cyber criminals to identify and exploit vulnerable drivers and strategies to mitigate these types of threats will be examined.
- Verona
- Via Belgio 16, 37135

056b Seminar (ISC)2 Italy Chapter – The Business Continuity
- Preparing for the future: navigating uncertainty with resilience and determination
- October 5, 2023
- 17:30
- Speakers/Guests: Fabrizio Cirilli
See you on October 5 to talk about business continuity and resilience in ICT. In this space I will also discuss the cyber risk management tool (CREST).
An opportunity for us all to reflect together, on increasingly topical issues, and clarify terminology in the context of articulated but vital activities in the event of an attack.
- Web

056 Cybersecurity: anticipating the future
- How Public Administrations and Companies Move, the Effectiveness of Futures Thinking
- Thursday, October 5, 2023
- 10:00 a.m.
- Speakers/Guests: Mauro Cicognini
What are organizations doing to defend themselves in cyber security? What is the importance of Future Thinking and anticipatory thinking in strategic foresight? As Clusit, the Italian association for cyber security that will also be the host of the event, confirms, there is a need for protection and prevention measures that nowadays entities and companies can no longer neglect.
These are just some of the topics that companies, with our Mauro Cicognini, journalists and industry experts will discuss during the daylong event.
- Cagliari
- Convento San Giuseppe

055 CREST SEMINAR
- Cyber Risk Evaluation Support Tool
- Monday, October 2, 2023
- 18:00 - 19:00
- Speakers/Guests: Fabrizio Cirilli
Next October 2, at 6 p.m. Fabrizio Cirilli will give a Webinar presentation to our CREST software for risk assessment according to ISO/IEC 27001:2022, distributed in SaaS mode.
Free access to CREST will be made available to all participants.
- Rexilience
- Web

054 DIGITAL DEFENSE
- Innovations and Trends in Cybersecurity
- 28/09/2023
- 18:00 - 22:00
- Speakers/Guests: Corrado Giustozzi
Innovations and Trends in Cybersecurity
28/09/2023
La Collina Dei Sogni
Albano Sant’Alessandro (BG)
- La collina dei sogni
- Albano Sant'Alessandro

053 – 6 MINUTES to breach your IT infrastructure
- Confindustria Belluno, SCP, Margas and CLUSIT advocacy
- Thursday, September 14
- 4:00 p.m.
- Speakers/Guests: Mauro Cicognini, Alessandro Vallega
A conference that will demonstrate live what happens during a hacker attack and how cyber criminals manage to get into companies. Most importantly, how to prevent dangerous situations, limit risks and prepare to resume business operations as quickly as possible.
- Rexilience
- Sala Caldart - Villa Doglioni Dal Mas, Via San Lucano (Belluno)

052b Business Continuity
- Sept 8, 2023
- 12:30
- Speakers/Guests: Fabrizio Cirilli
Preparing for the future: navigating uncertainty with resilience and determination
Fabrizio Cirilli, Project Leader and Author
Dealing with topics such as Business Continuity in the ICT world has never been an easy task: beliefs, myths and standards come together in a mix of endless arguments and interpretations.
In the document you will then find what is necessary to clarify the possible relationships between DR and BC, how these can be developed and articulated in compliance with existing standards, a list of standards to refer to, and other elements of clarification that we hope will be useful for correct interpretation and application in the company.
- Web
- https://www.isc2chapter-italy.it/nuovo-whitepaper-sulla-business-continuity/

052 Alphaville – Radio della Svizzera Italiana
- Security and geopolitical issues
- July 24, 2023
- 12:30
- Speakers/Guests: Corrado Giustozzi
On Monday, July 24, Corrado Giustozzi will be live from 12:30 to 1:00 p.m. on the Alphaville program of Radio della Svizzera Italiana (RSI Rete Due) to talk about security and geopolitical issues surrounding the U.S.-China competition over undersea cables for information transport.
The broadcast will be streamed on RSI’s website and the podcast will be embedded here.
- Web Radio Streaming
- https://www.rsi.ch/play/radio/livepopup/rete-due

051 – 24 | with Enrico Pagliarini | Radio 24
- The technological innovations that are changing the world
- July 21, 2023
- Today at 22:45 and Sunday at 14.00 (extended version)
- Speakers/Guests: Corrado Giustozzi
Corrado Giustozzi will take part in the broadcast to talk about ransomware attacks toward public administration and possible prevention measures.
Today at 22:45 and Sunday at 14.00 (extended version)
- Web Radio Streaming
- https://www.radio24.ilsole24ore.com/programmi/2024

050 PRIVACY
- DIGITAL COMMUNICATION AND THE IMPACTS ON PRIVACY
- July 20, 2023
- 17:00 - 18:00
- Speakers/Guests: Corrado Giustozzi
On Thursday, July 20 at 5 p.m. Corrado Giustozzi will participate in the webinar “Digital Communication and the Impacts on Privacy,” which will be streamed live by Officine Dati.
Corrado will speak specifically about the problem of encryption in mass communications, i.e., the difficult relationship between individual privacy and national security.
Moderator: Nicola Fabiano, vice president of Officine Dati.
Participants: Matthew Wild, Executive Director – XMPP Standards Foundation, Giuseppe Alverone, Data Protection Officer.
- Web Streaming roundtable discussion
- https://lnkd.in/dV_Z4m_z

049 CREST SEMINAR
- Cyber Risk Evaluation Support Tool
- July 17, 2023
- 17:00 - 18:00
- Speakers/Guests: Fabrizio Cirilli
Next July 17, at 5 p.m. Fabrizio Cirilli will give a Webinar presentation to our CREST software for risk assessment according to ISO/IEC 27001:2022, distributed in SaaS mode.
Free access to CREST will be made available to all participants.
- Rexilience
- Web

048 Digital Evidence In The Criminal Process
- Cyber Security and Privacy
- July 5, 2023
- 15:00 - 18:00
- Speakers/Guests: Corrado Giustozzi
- Courtroom B GUP, ED. A, Judicial City
- CRIMINAL CHAMBER OF ROME

047 YOU MAKE A HOLE IN ONE!
- ONE PROVIDER FOR ALL OF YOUR COMPANY'S DIGITAL SERVICES
- June 29, 2023
- 9.30 - 14.30
- Speakers/Guests: Alessandro Vallega
CONNETICAL
- c/O GOLF CLUB "LA MONTECCHIA"
- Via Montecchia, 12, 35030 Selvazzano Dentro PD

046 The evolution of cybersecurity in the age of artificial intelligence
- The evolution of cybersecurity in the age of artificial intelligence
- June 23, 2023
- 14.30
- Speakers/Guests: Corrado Giustozzi
Opportunities and Challenges.
- UNIVERSITÀ DEGLI STUDI LINK | Antica Biblioteca
- Via del Casale di San Pio V, 44 - Roma

045 Cybersecurity: NIS2 and DORA
- June 22, 2023
- 17.30
- Speakers/Guests: Corrado Giustozzi
Thursday, June 22 at 5:30 pm new meetup at Binario F in Meta.
This time we will talk about Cybersecurity by analyzing together with many experts the technical and legal aspects of the new European rules (NIS2 and DORA)
- meetup at Binario F di Meta
- Web

044 Healthcare Security Summit 2023
- Healthcare Security Summit 2023
- June 15, 2023
- 10.00
- Speakers/Guests: Alessandro Vallega
On June 15, we look forward to seeing you at the third edition of Healthcare Security Summit 2023, the virtual dedicated event on cybersecurity in healthcare.
Moderator: Alessandro Vallega.
- Web

043 RISCHIO CYBER 2024 – Roma
- RISCHIO CYBER 2024 - Roma
- May 31, 2023
- 15.30
- Speakers/Guests: Corrado Giustozzi
How you can help public administration and companies understand the challenges they will face in the months to come.
A unique opportunity to raise awareness of the danger, to understand the sources of risk and how attackers operate, and thus to make good choices on how to deploy the limited resources available.
The event is organised by Clusit Community for Security in partnership with Rexilience, Studio Legale Ristuccia Tufarelli & Partners and MM SpA.
At the end of the event, the book “Rischio digitale Innovazione e Resilienza” and free access to the CYBER RISK software for risk management according to ISO/IEC 27001:2022 will be distributed.
Attendees: Fabrizio Cirilli, Cosimo Comella, Luisa Franchina, Giovanni Gelpi, Corrado Giustozzi, Marco Locatelli, Paola Meroni, raffaele munari, Pieraldo Pistocchi, Stefano Quintarelli, Eliana Sessa, Luca Tufarelli, Alessandro Vallega.
- Sala Grande
- Piazza Cavour, 17 – 00193 Roma

042 RISCHIO CYBER 2024 – Milano
- RISCHIO CYBER 2024 - Milano
- May 30, 2023
- 15.15
- Speakers/Guests: Alessandro Vallega
How you can help companies and public administration to understand the challenges they will face in the months to come.
A unique opportunity to raise awareness of the danger, to understand the sources of risk and how attackers operate, and thus to make good choices on how to deploy the limited resources available.
The event is organised by Clusit Community for Security in partnership with Rexilience, Studio Legale Ristuccia Tufarelli & Partners and MM SpA.
At the end of the event, the book ‘Digital Risk Innovation and Resilience‘ and free access to the CYBER RISK software for risk management according to ISO/IEC 27001:2022 will be distributed.
Attendees: Fabrizio Cirilli, Cosimo Comella, Luisa Franchina, Giovanni Gelpi, Corrado Giustozzi, Marco Locatelli, Paola Meroni, raffaele munari, Pieraldo Pistocchi, Stefano Quintarelli, Eliana Sessa, Luca Tufarelli, Alessandro Vallega.
- Sala Centrale
- Centrale dell’Acqua (Piazza Diocleziano, 5 – 20154 Milano)

041 AIIC 2023 – National Conference Italian Association of Clinical Engineers
- Risk in supply chains
- May 12, 2023
- 9.30
- Speakers/Guests: Alessandro Vallega
We will talk about cyber attacks in healthcare – the evidence gathered by Clusit
Alessandro Vallega (Senior Partner rexilience, CLUSIT Italian Association for Information Security, Milan)
Please note that the session will be in Italian.
- Room 1
- Fortezza Da Basso - Florence (IT)

040 How to deal with supply security in practice
- WEBINAR Cybersecurity & Data Protection
- May 10, 2023
- 14.30 - 15.30
- Speakers/Guests: Alessandro Vallega
More and more often one hears about Supply Chain Security, and companies and public administrations have realised that their degree of security also depends on that of their suppliers. Incidents of course there were. In addition, there are increasing compliance obligations that require the company to control its supply chain.
In this webinar, the problem is explained and organisational approaches, best practices, compliance obligations and opportunities for improvement of the Third Party Process Management (TPRM) process are presented.
The session is in Italian.
- Webinar
- https://www.osservatori.net

039 Cybersecurity beyond artificial intelligence
- #cybersecurity, #ai
- May 10, 2023
- 10:20
- Speakers/Guests: Mauro Cicognini
With Mauro Cicognini, Founding Partner of Rexilience and Scientific Committee of #Clusit, we will talk about the cybersecurity scenario today and how it has changed in recent years.
Here the LN post with pictures of the event
Session in Italian.
- Centro Congressi Villa Ottoboni
- Padova

038 Cyber exposure of Italian SMEs
- Risk in supply chains
- April 19, 2023
- 17.30
- Speakers/Guests: Mauro Cicognini
We will talk about third-party risk in supply chains, and the specific exposure to it for Italian SMEs, within an event by Confartigianato Treviso.
Please note that the session will be in Italian. Attendance to this event is reserved to Confartigianato members and invitees of theirs.
- Confartigianato Marca Trevigiana
- Piazza delle Istituzioni, 34/A - Treviso

037 Privacy Symposium 2023
- Supply Chain Security: Knowing and managing the risk effectively
- April 18, 2023
- 9.30
- Speakers/Guests: Mauro Cicognini
We will take part in the panel discussion on Supply Chain Security.
Please note that attendance to the Symposium is generally payable, but free passes may be available via the event Sponsors.
- Auditorium
- Campo Santa Margherita, 3689 - Venice

036 Privacy Symposium 2023
- Security Threats Evolution
- April 17, 2023
- 9.30
- Speakers/Guests: Mauro Cicognini
We will take part in the panel discussion on the evolution of threats to security and privacy.
Please note that attendance to the Symposium is generally payable, but free passes may be available via the event Sponsors.
- University Ca' Foscari - Mario Baratto hall
- Dorsoduro 3246 - Venice

035 Supply Chain Security
- March 16, 2023
- Speakers/Guests: Alessandro Vallega
Tommorrow we will be presented the book “Supply Chain Security” edited by the Community for Cybersecurity.
We will meet the audience at the CLUSIT Cyber Security Summit in Milan.
- UNAHOTELS Expo Fiera Milano
- Via Giovanni Keplero, 12 - Pero
034 Radio 24 Podcast
- Business continuity and cybersecurity
- Speakers/Guests: Corrado Giustozzi
The stop of Libero and Virgilio e-mail services for over 4 days, a particularly rare but also very serious episode, leads us to talk about of the all too often undervalued e-mail services. We try to understand how use them in a more conscious, shrewd and prudent manner.
But in week we have also recorded the shutdown of some services of Microsoft (and other companies). Preparing for such events is increasingly important, explains to 2024 Corrado Giustozzi, cybersecurity expert and partner at Rexilience.
- Online

033 Hackers: Soldiers of the 21st Century
- Cyber attacks as an instrument of political, social and commercial warfare
- March 16, 2023
- 18.00
- Speakers/Guests: Corrado Giustozzi
We will talk about “Cybersecurity: the dark side of the net”
- Coop Grondaie Siena | Streaming
- Strada delle Grondaie, 1 - Siena

032 More threats and more regulations for everyone
- Serious cyber attacks on the rise, especially in Europe
- Speakers/Guests: Corrado Giustozzi
Who are the perpetrators?
How is the EU defending its strategic infrastructure?
- Online

031 AI and cybersecurity
- January 25, 2023
- 12.00
- Speakers/Guests: Corrado Giustozzi
The webinar will present an overview of the relationship between AI and cybersecurity, exploring both the possible risks arising from the development of malicious AI and the vulnerabilities of AI to specific attacks aimed at deliberately misleading them. Among other things, we will try to answer the following questions:
- How vulnerable are AIs to targeted attacks and with what consequences?
- What attacks are possible against AIs and how can they be countered?
- Online

030 Cyberwarfare
- Jurists and technicians at the challenge of geopolitical changes
- December 14, 2022
- 14.30
- Speakers/Guests: Alessandro Vallega
3 panel discussions on topical issues: cyberwarfare and cyber resistence, digital forensics as a law enforcement tool for cyberterrorism and cyberwarefare, crypto-asset.
- University of Milan, Pio XII hall
- Via Sant'Antonio, 5 - Milan

029 Risk analysis and management
- December 13, 2022
- 14.30
- Speakers/Guests: Alessandro Vallega
The webinar presents the state of the art and how risk has entered EU laws and regulations, indicating best practices, methodologies and products that can be used.
- Online

027 The XIX ANSSAIF Congress
- December 3, 2022
- Speakers/Guests: Corrado Giustozzi
The XIX National Congress of “US ANSSAIF” will be held, of whose Scientific Committee I have the honour of being a member.
We has participate with a speech on the “unthinkable complexity” of cyberspace, one of the key factors at the root of modern cybersecurity problems.
The event has been held in person and remotely via streaming.
- Grand Hotel Palace | Streaming
- Via Vittorio Veneto, 70 - Rome

026 Business continuity, resilience, sustainability
- What may not have been said
- November 29, 2022
- 09.00
- Speakers/Guests: Fabrizio Cirilli
Tools for implementing resilience in our organisations; methodological approach and certification of management systems.
In addition to the chairmen Corrado Miralli, Physical & Cyber Security Manager, Saipem S.p.A. & Chair of BCI Italy Chapter and Alessandro Manfredini, Group Security & Cyber Defence, a2a & Chair of AIPSA, coordinated by SKY’s competent journalist Mariangela Pira, we presented the paper:
TOOLS FOR IMPLEMENTING RESILIENCE IN OUR ORGANISATIONS – a methodological approach and certification of management systems.
- A2A Group House of Energy and Environment
- Piazza Po, 3 - Milan

025 Net insecurity
- the uncomfortable legacy of hippie philosophy
- November 10, 2022
- 11.20
- Speakers/Guests: Corrado Giustozzi
We talk about the foundaments of Internet.
- Online

024 Third-party security and compliance risk
- November 9, 2022
- 17.20
- Speakers/Guests: Alessandro Vallega, Cesare Gallotti
We talked about supply chain security, processes and technologies.
- Online

023 ANSA Conference: AI, war and cyberwar
- Humanity augmented by artificial intelligence
- November 9, 2022
- 15.00
- Speakers/Guests: Corrado Giustozzi
The IV edition of the annual event dedicated to AI.
- Auditorium of Ara Pacis
- Lungotevere in Augusta - Rome

021 Secure by design
- The new cybersecurity norms for the automotive industry
- September 28, 2022
- 14.30
- Speakers/Guests: Corrado Giustozzi
Cyberspace: unthinkable complexity.
- Centro Congressi Area CNR
- Via Piero Gobetti, 101 - Bologna

020 Council of the Clusit Community for Security
- September 16, 2022
- 09.30
- Speakers/Guests: Alessandro Vallega
Brainstorming on the 10-year future of cybersecurity (and digital).
- The Westin Palace Milan
- Piazza della Repubblica, 20 - Milan

019 Innotech Community 2022
- Innovation meeting
- July 6, 2022
- 16.00
- Speakers/Guests: Corrado Giustozzi
The National Cybersecurity Strategy 2022-2026 and implications for enterprises.
- Hotel NH Collection CityLife
- Via Bartolomeo Colleoni, 14 - Milan

018 Physical and cyber security at Italian airports, the state of play
- June 23, 2022
- 14.40
- Speakers/Guests: Corrado Giustozzi
Cybersecurity of Transport Infrastructures.
- Hotel NH Collection Vittorio Veneto
- Corso d'Italia, 1 - Rome

017 Cybersecurity at Namex Annual Meeting
- June 22, 2022
- 11.15
- Speakers/Guests: Corrado Giustozzi
The Namex Annual Meeting is divided into three sessions. In the first part, has been discussed the development of new cloud and edge computing models that are designed to bring content closer to end customers. In particular, the progressive process of decentralization of Internet eXchange Points.
The second session introduced the state of the art of threats to network security and the progress of the national cybersecurity strategy.
Finally, the last part of our plenary was focused on the experiences of some of the leading game changers in the Italian digital market.
- Villa Miani
- Via Trionfale, 151 - Rome

016 Cyber Resilience in Times of Peace and in Times of Crisis
- June 16, 2022
- 17.30
- Speakers/Guests: Corrado Giustozzi
Organized in partnership with the Microsoft company and FB&Associati.
- The Dome Campus Luiss
- Viale Romania, 32 - Rome

015 Innovative enterprises: start-ups, SMEs and corporations for the competitive positioning of the country
- #WMF2022 Stage Future of Italy
- June 16, 2022
- 12.40
- Speakers/Guests: Stefano Quintarelli
Business has changed: start-ups, innovative SMEs, large companies that focus on technology are at the centre of the country’s industrial policy.
We must define the offer and image of Italian innovation to position ourselves on the international market.
- Online

014 Risk-based approach to Cyber Security: if not in healthcare… where?
- June 16, 2022
- 10.00
- Speakers/Guests: Alessandro Vallega
Doctors, risk managers, IT professionals and cyber experts will discuss the adoption of an approach to cyber risk that leverages the strong risk culture already present in healthcare. In order to understand the limiting factors and leverage the obvious opportunities that a multidisciplinary approach so present in healthcare can represent.
The initiative is organised by Clusit, in collaboration with AIIC, AISIS, ANRA, AUSED.
- Online

013 Cyberwar, paradigms and perspectives
- June 10, 2022
- 14.30
- Speakers/Guests: Corrado Giustozzi
We will give a speech as an internal professor at the opening conference of the 7th edition of the Master in Cybersecurity at Link Campus University in Rome.
- Link Campus University
- Via del Casale di San Pio V, 44 - Rome

012 ISPI: Cyber security in Europe
- Are we ready to defend ourselves?
- May 31, 2022
- 18.00
- Speakers/Guests: Corrado Giustozzi
Recent cyber attacks against Italian and European governmental and institutional entities have raised concerns about a potential cyber war, conducted within the broader framework of the conflict between Russia and Ukraine. What are the actual threats to national and EU security? What strategies have been implemented? And what are the models to be inspired by?
The event, organised by ISPI in collaboration with the Ministry of Foreign Affairs and International Cooperation.
- Online

011 Melog – Radio 24
- May 31, 2022
- 12.15
- Speakers/Guests: Corrado Giustozzi
We will be the live guest of Gianluca Nicoletti on his programme Melog on Radio 24 to talk about cyberwarfare and Russian attacks, real or presumed.
- Online

010 Secure your strategy
- May 20, 2022
- 09.00
- Speakers/Guests: Corrado Giustozzi, Alessandro Vallega
PART ONE | CYBERSECURITY YESTERDAY AND TODAY
Keynote “Cyber: a three thousand years long history”
PART TWO | STRATEGIES FOR CUTTING-EDGE SECURITY
“The asymptotic CyberSecurity: how to integrate your choices in the organizational rationality”
- Spazio Reale
- Campi Bisenzio - Florence
009 Electronics and recycling – TV and viewing distance – Antivirus made in Italy
- April 22, 2022
- Speakers/Guests: Corrado Giustozzi
Comment on the discussion going on in our country on the necessity and advisability of having IT security products such as antivirus developed in Italy.
- Online

008 Security Summit – Digital Risk, Innovation and Resilience
- March 16, 2022
- 18.00
- Speakers/Guests: Alessandro Vallega
The Clusit Community for Security, directed by Alessandro Vallega, introduced the thirteenth publication (free download from https://c4s.clusit.it) entitled “Innovation and resilience of digital risk” whose writing is the result of the collaborative work of 80 experts in the sector.
- Online

007 Security Summit – Step 2
- Streaming Edition
- March 16, 2022
- 09.00
- Speakers/Guests: Mauro Cicognini
With Dell Secureworks: Cloud Security – technologies in (R)evolution!
- Online

006 Security Summit – Step 1
- Streaming Edition
- March 15, 2022
- 16.40
- Speakers/Guests: Mauro Cicognini
With Dell Secureworks.
- Online

005 Cybersecurity the other side of digital
- December 1, 2021
- 16.30
- Speakers/Guests: Corrado Giustozzi
Rexilience participates to the webinar organized by the Italian Association for Computer Science and Automatic Computing on “Cybersecurity: the other face of digital”.
- Online

004 Calcūlo ergo sum
- November 26, 2021
- Speakers/Guests: Corrado Giustozzi
Respecting a tradition that is renewed since the first edition, we will be once again among the speakers of the beautiful Conference of Legal Informatics of the College Ghislieri of Pavia, now in its sixteenth edition and entitled this year to the memory of its founder and animator, as well as dear friend, Prof. Romano Oneda.
The conference, dedicated to the delicate topic of Artificial Intelligence, will be held in presence in the Aula Magna of the College in compliance with current anti-Covid measures, in particular with regard to the possession of Green Pass.
The speech of Prof. Giustozzi, entitled “Intelligent but naive: how to fool the AI” will focus on “adversarial attacks” aimed at confusing and deceiving artificial intelligence.
Admission is free but it is necessary to book your participation. The conference will also be streamed on the College’s YouTube channel.
The topic is juicy and the speakers are fantastic, so we invite you to attend!
- Collegio Ghislieri
- Piazza Collegio Ghislieri, 5 - Pavia

003 CLOUD PLANET – Rules, rights and duties in the cloud industry
- November 23, 2021
- 09.00
- Speakers/Guests: Alessandro Vallega
We talk about cloud for SMEs, between rights, development, security and revitalization.
Commendable initiative of Iusintech, with the participation of Guido Scorza (Consiglio del Garante per la protezione dei dati personali), Rita Eva Cresci (Iusintech), Maria Roberta Perugini (Iusintech), Giuseppe Fragola (MISE), Roberto Giacobazzi (University of Verona), Raffaele Conte (CNR), Paolo Costa (Spindoc), Roberto Moro Visconti (Università Cattolica del Sacro Cuore), Stefan Umit U. (4Securitas), Alessandro Vallega (Rexilience), Cesare Burei (MARGAS), Massimiliano De Gregorio (REVO Spac), Raffaele Barberio (Key4biz), Michele Zunino (Consorzio Italia Cloud), Jeff Zakar (Irideos), Laura Capodicasa (Irideos), Francisco Mingorance (CISPE).
- Online

002 Sensitive data and critical infrastructures: IT violations
- November 12, 2021
- 15.00
- Speakers/Guests: Corrado Giustozzi
In collaboration with Polis Open Learning.
- Sala Conferenze Palazzo Theodoli
- Piazza del Parlamento, 9 - Rome

001 EIDAS 2.0
- Security Summit - Streaming Edition
- November 10, 2021
- 12.00
- Speakers/Guests: Alessandro Vallega, Marco Locatelli, Silvio Sperzani
Connecting Europe in a secure way and respecting the rights and freedoms of individuals, necessarily passes through the issue of digital identity. With the new EIDAS regulation, the subject of this session, several things will change, such as the public system for managing the digital identity of citizens and businesses (SPID), the Electronic Identity Card (CIE) and wallets to authenticate and access services.
- Online

000 Security and Intelligence: new threats
- October 22, 2021
- Speakers/Guests: Corrado Giustozzi
Speakers: Antonino Vaccaro, Corrado Giustozzi, Fabio Sammartino, Lior Tabansky, Mirco Marchetti, Gabriele Carrer.
- Online
